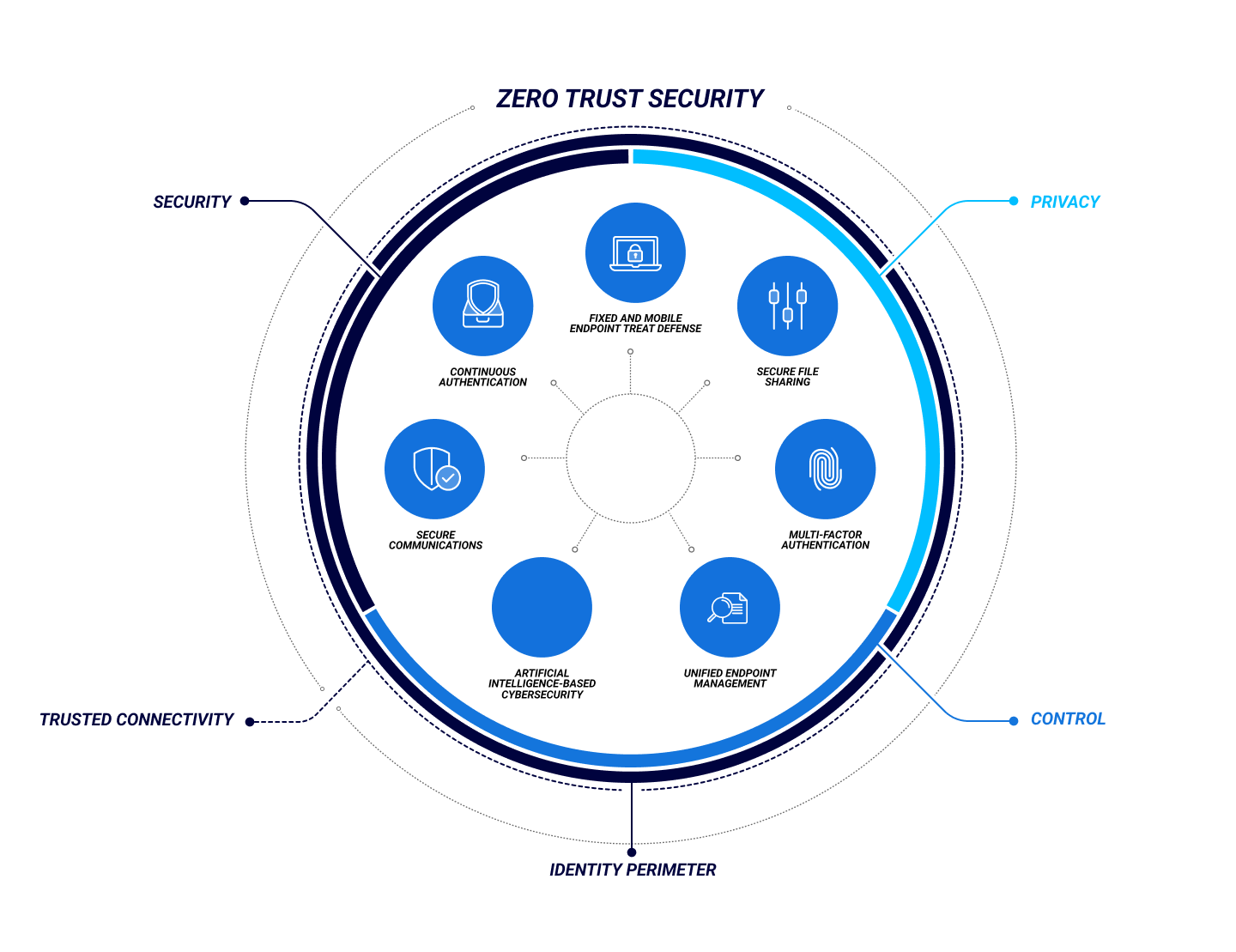
What Is Zero Trust Security?
Zero Trust Security is a cybersecurity framework that requires users prove who they are, that their access is authorized, and that they’re not acting maliciously before they can access an organization’s digital assets and network.
As the modern hybrid work environment has rendered traditional, on-premises network-based security models obsolete, Zero Trust Security has risen in prominence as a means to protect an organization’s data and people—especially as remote work and cloud-based services become the norm.
According to Forrester, Zero Trust Security denies users’ access to applications and data by default. It assumes that there is no longer a traditional network edge, taking a much more stringent, continuous, and dynamic approach to user authentication. The challenge, then, is ensuring that Zero Trust Security is seamless enough to avoid impacting the user experience.
Zero Trust Benefits
Reduced Business Risk
Unified Access Control
Reduction in Breaches
Compliance Support
How Zero Trust Works
The critical difference between Zero Trust and traditional security systems is that authentication is never assumed but denied by default. With traditional security, once access has been granted within the network perimeter, it typically persists either permanently or for an extended period without the need for refresh. In contrast, Zero Trust continuously monitors user’s behavior and validates that they and their devices have the proper privileges and attributes. The risk associated with the user, their device, and context is taken into account based on real-time visibility of user and application activity.
Zero Trust leverages a variety of identity attributes to maintain optimum levels of security during access to enterprise or cloud assets, including:
- Type of credential providing user identity verification.
- Privileges associated with credentials.
- Context, including device location (within corporate premises or in a public space) and user behavior.
- Continuous authentication, potentially including multi-factor and background biometrics.
- Device health, including operating system versions, patch levels, and firmware updates.
- Applications installed on endpoints, assessing those that could pose a threat.
- Detection of suspicious activity from user, device, and context.
Zero Trust Security constantly and dynamically monitors these attributes, applying analytics and AI/ML to provide a proactive policy response. Most cyberattacks are against credentials and identity stores, so this dynamic threat monitoring ensures greater system integrity.
Zero Trust Security isn’t a single product or service but a methodology backed by an ecosystem. For that reason, it may not entail a wholesale replacement of existing security infrastructure. An organization could already have some components in place that will be valuable for the journey towards Zero Trust. Considering that you will also need to take your users on this journey, maintaining familiar processes and practices will help smooth the transition.
The assessment of an organization’s readiness and steps required for the implementation of Zero Trust revolves around how identity is articulated in an organization, which could be at one of these four stages:
1. Fragmented Identity
2. Unified Identity and Access Management
3. Contextual Access with Automated Provisioning
4. Adaptive Workforce
Once an organization’s security or IT team has assessed what phase its identity systems are at and their readiness for Zero Trust, it can begin to implement the methodology.
Implementation involves three broad stages:
1. Visualization
2. Mitigation
3. Optimization
Implementing a Zero Trust access control model isn’t necessarily a simple task to undertake.
Organizations who understand the tremendous benefits to be realized and are determined to implement a Zero Trust architecture can expect to encounter several challenges along the way, including:
Technology Silos
Legacy operating systems and applications, development tools and platforms, third-party applications, and services along with “homegrown” applications and many others
Lack of Technology Integration
Hurdles can emerge with owned and third-party platforms—any issues with these integrations can easily derail a Zero Trust implementation.
Rapidly Changing Threat Surface and Threat Landscape
This can potentially lead to challenges with technologies that are limited in deployment modality.
FAQ
What is Zero Trust Security?
Zero Trust Security is a cybersecurity system whose default mode is not to trust entities such as users and their devices. Regular reauthentication ensures a higher level of integrity for infrastructure and application access, providing greater protection against cyber threats in a hybrid work environment.
Why is Zero Trust Security important?
With the rise of remote and hybrid work and the proliferation of mobile devices used both on- and off-premises, how we access applications, data, and services has changed. Business applications range from traditional on-premises software to containerization and the cloud. Zero Trust Security provides a solution to this varied access scenario.
What is a Zero Trust Assessment?
A Zero Trust Assessment is an organization’s measurement of how mature its existing processes are for implementing Zero Trust Security. This assessment focuses on how the organization handles identity, which can be at one of four stages:
- Fragmented Identity, where different logins are used for each service
- Unified Identity Access Management enabling a Single Sign-On and Multi-Factor Authentication across all resources
- Contextual Access with Automated Provision that adds dynamic policy adjustment based on context
- Adaptive Workforce in which the organization is ready to integrate new security technologies as they arrive.
What is a Zero Trust eXtended (ZTX) ecosystem?
Zero Trust eXtended (ZTX) is a development from Forrester that expands Zero Trust Security across a company’s entire digital ecosystem—beyond mere network segmentation and with a focus on identity and data. A ZTX ecosystem includes the entire suite of services and platforms an organization needs for a successful Zero Trust Security implementation.
What are the 3 stages of the Zero Trust Security Model?
Zero Trust Security Model implementation happens in three stages:
- Visualization reveals the company’s resources, access points and associated risks.
- Mitigation then detects and prevents potential threats.
- Optimization extends protection to every aspect of the IT infrastructure regardless of location on- or off-premises while providing the best possible user experience.
What is Zero Trust Architecture?
Zero Trust Architecture is built around the principles of Zero Trust Security, using a series of components designed to make continuous authentication robust and as seamless as possible to the end user. The users are strongly authenticated in a continuous but unobtrusive fashion. In parallel, the devices that they use are constantly monitored for compromise.